The Cost of Breaches Associated with Endpoint Security

The occurrence of cyber-attacks has seen a steady uptick lately. For the worst, experts predict that with hackers leaving no stone unturned to take advantage of even a minute weak spot, the scenario may only deteriorate in the future.
According to this research conducted by the Ponemon Institute; the average cost of endpoint attacks has increased from an average of $7.1 million to $8.94 million. Furthermore, 68% of the respondents registered that the frequency of attacks against endpoints have increased over the past 12 months.
So, if you are a stakeholder, these figures may throw light on why you should be considering cybersecurity seriously.
Further, with a considerable percentage of the employee community working from home during the pandemic, endpoint security has become pivotal in the remote paradigm.
Having said that, let’s dive deeper into the intricacies of endpoint security.
Table of Content
Why is Endpoint Security Important?
Your network connectivity is the heart of your business. Employees connect over networks to access data through desktops, laptops, and mobile devices.
Hackers use these endpoint devices to gain access to your network and steal information. To put it short, when your employees use a medium/device to communicate/share information without appropriate guardrails in place, it gives room to vulnerability.
Endpoint security is important because these devices are considered to be the weakest
spots that can be easily used by hackers.The implementation of an effective endpoint security management solution will contribute towards maintaining a definite level of safety and security.
What Are the Challenges in Maintaining Endpoint Security?
Bring Your Own Device (BYOD) has been broadly adopted by organizations. Though this practice supports workforce mobility and remote work, it also comes with its own set of bottlenecks.
Let’s consider a real-world time scenario to understand this better.
A renowned organization has a distributed workforce and supports a remote work culture. The employees are free to use their devices and connect over personal networks to perform their everyday activities. This includes sharing and processing sensitive payroll and finance-related information too.
In this situation, consider a malicious actor trying to gain access to this organization's payroll management system. The first factor targeted will be the device used by the controller of payroll. Most employees tend to overlook the need to have a strong password. In the event of the employee device being used on an exposed network, the hacker may easily crack the password and compromise payroll-related information.
The aftermath of this cyberattack can be financially catastrophic. The hacker may gain access to the payroll management system, meddle with critical data, and even be involved in the anonymous transfer of funds.
Thus, is the challenge and impact of endpoint security.This was, however, just one effect of an endpoint security attack. Let’s look into the others in detail.
The Cost of Data Breaches You Will Need to Incur Due to Endpoint Security Attacks.
Check out the figure below to know the cost of data breaches due to endpoint security attacks.
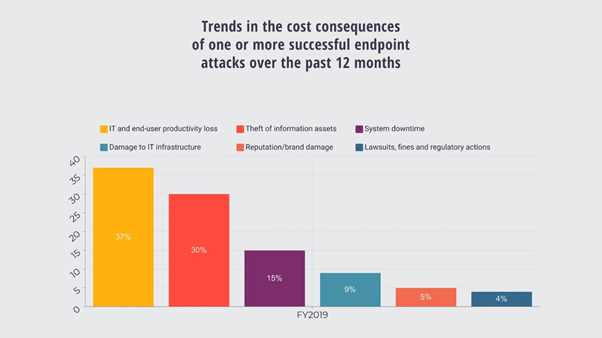
Here are a few costs you will have to pay for due to endpoint security attacks.
1. The Considerable Loss of Productivity
The major cost that companies need to pay when they fall prey to endpoint attacks is the loss of productivity.
With several organizations joining the bandwagon of remote work and distributed workforces, in the case of an endpoint attack, the hackers are more likely to gain control over endpoints and hinder productivity. When companies are not able to function to their full capacity, it results in a loss of productivity thereby contributing towards a decline in revenue.2. Interrupted Services or System Downtime
Downtime can be disastrous for organizations irrespective of their sizes.
The interruption of services due to an endpoint attack can hurt the bottom line of businesses. With companies not being able to operate normally, they may miss critical deadlines. This, in turn, results in the loss of reputation further leading to a drop in client acquisition.
3. Loss of Critical Business Information and Legal Costs
The impact of an endpoint attack is not just limited to hindering your normal operations but also includes damages to servers, locked data, or hard drive failures due to malicious code operating on them.
Apart from financial loss and decline in productivity, you may need to deal with costs of class action suits, provide compensation to your clients due to breaches of consumer data, or face regulatory fines under the laws of your state/country.
Dealing with Endpoint Attacks
Endpoint attacks can be significantly mitigated by:
a. Nurturing a Cyber Aware Employee Workforce
Employees are more like the human firewall for your company. Therefore, the first thing to focus on
is to educate them about endpoint security best practices, especially in a BYOD scenario.This should include being vigilant when using public networks and having strong passwords to guard sensitive information.
b. Implementing a State-of-the-art Endpoint Security Management Solution
Having a unified endpoint protection management solution helps:
- Obtain improved visibility across the organization
- Enhance control over data exposure, implement stringent authentication methods with zero trust
- Facilitates the implementation of robust endpoint threat defense management solutions to deliver risk-based conditional access that protect applications.
- Experience unified mobile device management platform across different device types and operating systems
Unified Endpoint Management with IBM MaaS360
We are an IBM business partner and specialize in delivering unified endpoint protection solutions like IBM MaaS360. This next-gen unified endpoint protection solution stands out due to its capabilities that facilitate organizations to better protect critical endpoints, content, and data.
Unified Endpoint Management breaks down the complexities in handling your mobile assets from laptops, personal and corporate-owned devices. IBM MaaS360 offers a cognitive approach to unified endpoint management.
IBM MaaS360 helps in:
- Protecting and efficiently handling the remote workforce
- Controlling the risks of mobile threat defense
- Improving responses with Watson AI
- Seamlessly integrate identity and access management with UEM
Click here for a free trial and a deeper delve into our offerings!
Wrap Up:
The risk of endpoint attacks is increasing and organizations need to incorporate a competent endpoint security solution.
The points mentioned above will throw light on the cost/loss organizations experience in the event of an endpoint attack.To know more about our offerings and solutions, feel free to contact us for further clarifications. Click here for a free trial or you may also drop us an email at cybersecurity@quantumstrides.com.
About Quantum Strides
Quantum Strides is a connoisseur in a plethora of cybersecurity offerings that include but are not limited to enterprise-grade threat defense that encompasses detection, automated remediation, and adherence to compliance regulations.


WRITE A COMMENT