Dark Web Monitoring

The number of cyberattacks has seen an alarming increase lately. To add on, the approaches of hackers are also constantly evolving. While most organizations follow a reactive strategy that involves defending a cyberattack after it occurs, it is important to consider that predicting, identifying, and mitigating cyber risks is equally pivotal. That is, it is high time organizations adhere to a proactive approach that altogether helps keep cyber risks at bay.
Consider a scenario wherein your corporate email address has been exposed in a third-party data breach. Cybercriminals can use this information to plot credible phishing emails against you, impersonating the third-party service you were enrolled in.
To worsen it, exposed credentials of your employees can be used to access corporate applications, systems, and networks to steal data, execute fraud, install ransomware, or use you as the go-between to target a larger partner or customer.
According to this survey by Statista, 54% of the participating MSPs indicated that phishing scams were the most common cause of ransomware.
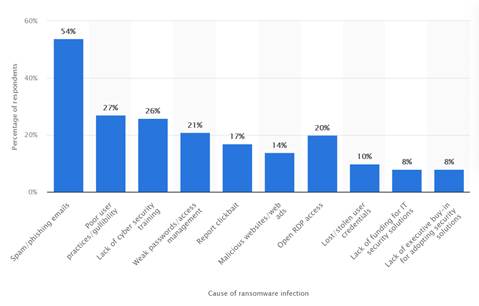
Table of Content
Why Should You Care About the Dark Web?
Closely monitoring the dark web is one way you can predict an upcoming cyber-attack and steer clear away from it.
The dark web is a subset of the internet that can be accessed by using special software or browsers by people who prefer to remain anonymous.
This dark web is used by cybercriminals to coordinate and execute cyber-attacks using stolen data. It also contains sensitive information about businesses and can cause a considerable amount of damage through illegal access to your organization’s confidential information.
How Can You Safeguard Your Sensitive Information?
Try finding if any of your proprietary information or confidential information has been stolen and is available on the dark web. Furthermore, the attackers may even begin a discussion about planned attacks. If the name of your organization or any data about future attacks is found on the dark web, you should consider formulating an action plan to evade the cyber threat.
Moreover, you may be exposed to information about tools/software that is being developed and traded to harm or misuse your kind of technology stack.
This kind of visibility is important because it helps you to improve your security posture by proactively identifying threats thereby allowing you to reduce cybersecurity risks.
How Does Monitoring the Dark Web Help Assess Cyber Risks?
Monitoring of the dark web helps assess cyber risks in the following ways:
1. Enables Proactive Detection of Third-party Breaches
If your business involves the contribution of third-party vendors, constant monitoring of the dark web can help you obtain insights about vendor breaches or ransomware attacks.
You could lay your hands over this critical piece of information even before your vendor realizes the occurrence of an attack. Equipped with this information, you may evolve your approach in involving vendors within your work ecosystem.2. Helps in Identifying Credential Data Leaks
By monitoring the dark web, you can identify potential emails and passwords that have been leaked over the dark web. You can proactively recognize credential stuffing attacks before they occur and workaround to change the compromised passwords. Furthermore, it also helps to monitor data lumps containing your IP addresses.
How to Respond if your data is exposed in the Dark Web?
- Begin with focusing on threats that are relevant to your organization. Determine the most suitable use cases and try to create an early detection and remediation strategy.
- Ensure to have stringent security protocols in place when dealing with third-party vendors. Though all the third-party vendors may not be treated equally, it is important to have appropriate security controls when sharing sensitive information like your clients or employee details.
- Continuously monitor the dark web for other employees’ stolen credentials and provide valuable inputs to your team that slashes down the time-to-detection and remediation of cyber risks.
How Can You Prevent Your Information from Landing on the Dark Web?
Here are a few ways you can use to reduce the odds of your sensitive information landing on the dark web.
- Maintain a Cyber Aware Workforce
Ensure that your workforce is educated about malicious links and phishing emails. Offer regular cyber awareness training to make them wary about suspicious links and prevent them from clicking such links.
- Implement Strong Password Policies
Having a strong password policy is cardinal. Ensure that your workforce is diligent to change passwords at regular intervals. It is also important to maintain strong passwords. Educate your employees to take the help of a password manager to generate strong passwords every time they need them.
- Ensure to Browse Securely
Avoid connecting over a public network or sharing sensitive information when using them.
It is most secure if you connect over a Virtual Private Network (VPN) or at least your private network if you need to work on confidential information. You can double-check the status of the network by looking at the URL. The URL should necessarily begin with HTTPS or the browser you are using should have a padlock sign/the word “secure” in it.- Regulate the Use of External Devices
Limit the use of USB and HDD plugs. This will eliminate the chances of data breaches and the entry of malware or any unknown threat.
Wrap Up
With hackers leaving no stone unturned to gain access to critical organizational information, the dark web is a lesser-known space that businesses should keep an eye on. This post elaborates on the different intricacies of the dark web and how companies can prevent their sensitive data from reaching the dark web. It also throws light on the fact that by monitoring the dark web, businesses are equipped with threat intelligence which proves to be a pivotal mitigation tool in their cybersecurity arsenal.
Click here for a free trial of our human risk management solution dovetailed with the dark web monitoring feature and explore more of our capabilities!
About Quantum Strides
Quantum Strides is a connoisseur in a plethora of cybersecurity offerings in the Human Risk Management domain, that include but are not limited to awareness training, phishing simulations and dark web monitoring for corporate stolen credentials.
If you are interested to know more about our platter of cybersecurity offerings, feel free to contact us or drop us an email at cybersecurity@quantumstrides.com


WRITE A COMMENT