Vulnerability Management
Cybersecurity is crucial for organizations of all sizes. Digital transformation and cloud adoption have expanded the attack surface, while the shortage of Cybersecurity skilled professional make it even more difficult to effectively protect organizations’ information assets.

For example, consider the recent Log4j vulnerability that allows malicious attackers to execute their code on a targeted system remotely. Overcoming this vulnerability will be a huge challenge, considering the widespread use of this library on software applications and Internet-facing systems.
This instance proves that though staying cyber aware is pivotal, it is equally important to constantly check on emerging vulnerabilities, and especially for known exploited vulnerabilities.
Organizations discover several vulnerabilities from time to time. They may be a result of unpatched operating systems and applications or exposed systems that hurt the security configuration of your network.
But how can these vulnerabilities be dealt with? Is there an approach to identify them proactively?
Let’s understand them in detail.
What Is a Vulnerability and How Can It Be Managed?
A vulnerability is defined as a risk or any external factor/element that gains unauthorized access/privileged control to your network/application/endpoint or server. A few examples of a possible vulnerability may be communication ports that are used on public networks, unpatched/insecure configurations of software/operating system (OS), or increased exposure that may allow malware to corrupt your system.
According to NIST vulnerability analysis report 2020, the maximum number of security vulnerabilities were disclosed in 2020 (18,103). This amounted to an average of 50 Common Vulnerabilities and Exposures (CVEs) per day.
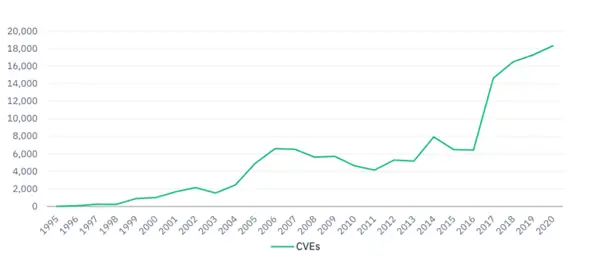
With the rising number of vulnerabilities and the security threats as a result of these, the need of the hour is to have a precise prioritization and remediation strategy in place. Security scans can no longer be a periodic occurrence, they need to be an integral part of your organizational processes, backed by automated tools. This is possible only when you consider the implementation of a comprehensive vulnerability management policy.
In a nutshell, vulnerability management is a continuous process that should be used to identify and remediate vulnerabilities through patching and appropriate configuration of security settings. This will provide a holistic view that supports informed decision-making with regards to which vulnerabilities need to be addressed in priority and mitigated accordingly.
What Are the Steps Involved in Vulnerability Management?
The process of vulnerability management can be categorized into the following:
1. Identification of Vulnerabilities
Vulnerability management focuses on the identification of vulnerabilities. This is done through scanning of vulnerabilities including four stages:
- Scanning of network-accessible systems by either pinging them or sending them TCP/UDP packets.
- Identification of open ports and services running on these scanned systems.
- Logging into/accessing systems remotely to obtain detailed information wherever possible.
- Relate the system information with existing/known vulnerabilities.
2. Evaluation of Vulnerabilities
The next step after the identification of vulnerabilities is their evaluation. A vulnerability management solution will help provide risk ratings and scores for vulnerabilities based on an open industry standard for assessing the severity of computer system security vulnerabilities, CVSS. This score will help you to decide on which vulnerabilities to focus on first.
A few other important factors to be considered when evaluating vulnerabilities are as follows:
- What is the nature of the vulnerability? Is it true or false positive?
- Is this vulnerability exploitable directly from the internet?
- What is the difficulty level to use this vulnerability in your network?
- Does this vulnerability include a published exploit?
- What may be the impact on your business if this vulnerability was exploited?
- Are there any security controls in your network that may reduce the negative impact of the vulnerability, if exploited?
- How long has the vulnerability existed in your network?
- Have you considered differentiating theoretical vs actual cyber risks in your technical landscape? This will help in better prioritization.
3. Neutralizing the Vulnerabilities
The next step after identifying and evaluating the vulnerabilities is treating these vulnerabilities. This includes the following processes:
- Remediation This involves completely patching and fixing a vulnerability to curb further exploitation. This is the best solution you should be aiming at.
- Mitigation Mitigation involves reducing the impact of the vulnerability on your network/system if exploited. This helps if an appropriate fix cannot be found for a vulnerability.
- Acceptance Accepting a vulnerability as is involves taking no action against an identified vulnerability. This is usually done when the vulnerability is deemed to be a low-risk one.
4. Reporting the Vulnerabilities
Vulnerability management solutions offer several options to report and visualize comprehensively scanned vulnerability-related data. Ideally, the reports are projected through customizable dashboards. This helps your security team to easily interpret the risks of vulnerabilities and look for appropriate remediations around them. Further, these intuitive insights support you in consistently monitoring the vulnerability trends again contributing towards the improvement of compliance and regulatory requirements.
How to Develop an Effective Vulnerability Management Program?
Establishing an effective vulnerability management program takes time. Following the below-listed best practices will help develop an effective vulnerability management program with minimal refinements over time.
Conducting Penetration Testing at Regular Intervals of Time.
Penetration testing supports your security team to understand in detail the way attackers may operate. Furthermore, it offers an objective view of the strength of your protection/mitigation techniques in place.
As penetration testing utilizes state-of-the-art techniques and tools, it helps find emerging vulnerabilities and contributes towards addressing them promptly. It also offers a realistic view of your security posture along with enabling them to allocate sufficient resources that can help respond to attacks effectively.
Tracking and Keeping Account of All Your IT/OT Assets
Keeping track of all your IT/OT assets and accounts is pivotal to proactively identify vulnerabilities. Appropriate tracking of IT assets also offers you a chance to clean up. That is, when maintaining an account of assets, you may most likely bump into legacy systems, applications that aren’t being used, and data that doesn’t have value. Removing these assets helps reduce liability and boosts your system performance.
However, manual scanning of your systems including laptops and desktops may not be possible. Using automated tools and techniques will help locate the required assets thereby reducing vulnerabilities due to outdated/unused devices and applications.
Maintain Comprehensive Data for Intuitive Insights
Interactive education/training about risks can help minimize risks though they cannot be eliminated. For example, human risks majorly contribute towards creating vulnerabilities. While user permissions cannot be controlled altogether, educating the users about the risks of a compromise and things at stake when your system undergoes a breach can help reduce such instances.
This can be done by offering visually appealing data that help your users understand the importance of mitigating these risks by timely identification and reporting.
Stay On Top of Threat Intelligence
Though there are several ways to identify security risks and mitigate them, limiting your exposure will result in you overlooking numerous risks thereby proving fatal to your technical ecosystem.
Improving your level of threat intelligence proves important. This can be done by participating in forums and obtaining knowledge from databases about information handling best practices. These forums/groups may provide you with knowledge about specific expertise that may lag in your in-house security team.
Wrap Up
Vulnerability management may not be always as easy as simply scanning, patching, and validating systems. Patching systems that are critical may result in downtime especially if a reboot of the system is involved. Furthermore, a few systems may function only on outdated operating systems wherein patches aren’t available. In these cases, it becomes important for standby security measures to be in place. These instances and many more can be handled seamlessly with a next-gen vulnerability management process.
Hopefully, this read may have provided you with critical insights about the various aspects of vulnerability management and how you can establish one effectively.
If you are looking to manage your vulnerabilities, feel free to reach out to us at cybersecurity@quantumstrides.com
About Us
Quantum Strides is a connoisseur in a plethora of cybersecurity offerings in the ransomware domain, that include but are not limited to vulnerability and penetration testing, awareness training, phishing simulations, and dark web monitoring for corporate stolen credentials.


WRITE A COMMENT