Why Is Data Encryption and Protection Tool like IBM Guardium Key for the Healthcare Industry
You may have heard a lot about cyber threats and how they can severely impact the bottom line of your business. Undoubtedly, you may have adopted one or many of the cybersecurity approaches to curb risks and prevent attacks. Ideally, you may also be using a state-of-the-art cyber risk monitoring system in place.
Having said that, we reiterate the importance of cybersecurity for organizations in the IT domain to function uninterruptedly. What about the healthcare industry? Do they face similar risks and threats too?
Let’s understand this in detail.
A Peek into the Cyber Threats in the Healthcare Industry
Though electronic healthcare records come with several advantages of enabling quicker access to critical patient information, easy data sharing, and eliminating the chances of fragmentation, they come with a set of cybersecurity challenges.
Electronic Healthcare Records (EHRs) contain critical patient information that proves to be a valuable commodity for hackers. Not just credit card numbers, patient account information, personal information, but EHRs have the medical history of patients that is updated after every visit and diagnosis. If this sensitive information lands in the hands of fraudsters/nefarious people, they may misuse it for identity theft or extortion. It may also result in holding information hostage in return for a ransom. This will delay treatment/medical assistance for the patients, hitting negatively on their health condition.
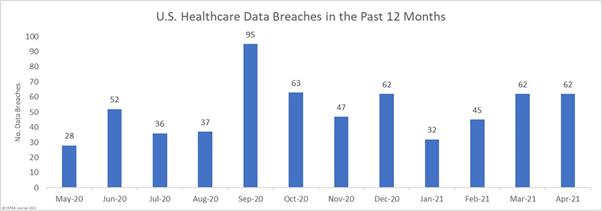
The below-shown data elaborates on the average number of breaches that have occurred as of May 2021. As we see, high numbers of records continue to be compromised. In fact, across the 62 breaches that happened in April, 2583117 health records were compromised.
That was about how cybersecurity is pivotal for the healthcare industry. Now, we have consolidated a few points on how a data encryption and protection tool like the IBM Guardium can help secure critical patient information. Check them out right away!
What Is IBM Security Guardium Data Encryption?
IBM Security Guardium Data Encryption (GDE) is a modular set of encryption solutions that helps in "data-at-rest" security across your organization. GDE is an integrated suite of products that are built on a common, extensible infrastructure. They also come with capabilities of centralized key and policy management that helps reduce administration efforts, addresses compliance-related concerns, data security policies while staying aligned with encryption best practices.
What Are Its Key Advantages?
The key benefits of adopting the IBM Guardium data encryption are as follows:
- Effectively protects and controls access to databases, files, containers, and critical applications.
- Protects assets on the cloud virtual environment, big data, and other physical environments.
- Improves responsiveness to security challenges and compliance requirements.
- Equips to combat external cyber threats and internal misuse of data.
- Addresses a range of security and privacy mandates like Payment Card Industry Data Security Standard, Health Insurance Portability and Accountability Act, and Federal Information Security Management Act to name a few.
What Are the Key Capabilities of IBM Security Guardium Data Encryption?
a. Guardium Data Encryption Data Security Manager
The IBM data encryption data security manager contains a suite of integrated products. It helps in the following ways:
- Enables to address compliance and data privacy standards without impacting the operational and functional aspects of the business process.
- Is non-intrusive, scalable, and easy to deploy the solution. These solutions do not require any changes to be made to existing applications, user workflows, or operational procedures.
b. Guardium for Tokenization
Guardium for tokenization reduces the cost and effort that goes into adhering to compliance and regulatory mandates. The solution provides data tokenization and dynamic display security. This plays an important role in protecting sensitive business assets. The solution can also be extended to leverage the cloud, big data, and outsourced models effectively.
c. Guardium for Cloud Key Management
This solution comes with Bring Your Own Key (BYOK) and Keep Your Own Key (KYOK) capabilities. It helps reduce the key management complexities and operational costs by providing a full lifecycle control of encryption keys with centralized visibility and management to the customers.
d. Guardium for Data Encryption Key Management
Guardium for data encryption key management helps customers who already have a data security manager to handle their encryption keys. Having centralized key management helps consistent policy implementation across the organization while reducing maintenance and training costs.
e. Guardium for File and Database Encryption
The benefits of using this solution are:
- Slashes down costs associated with encryption maintenance and implementation.
- Reduces the impact of encryption on the user experience.
- Accelerates the recovery of data encryption with older keys.
- Enables real-time encryption of unprotected data during the initial phase of deployment.
f. Guardium for Container Data Encryption
The key features of this solution include the following:
- Offers encryption, data access controls, and data access audit logging.
- Helps control data stored within containers and data accessible from containers.
- Helps in container-specific granular data access controls for particular users, processes, and resource sets.
- It doesn't require changing the settings of the application, containers, or infrastructure.
- Uses the same agents and infrastructure as Guardium for file and database encryption.
g. Guardium for Application Encryption
This solution streamlines the process of adding encryption into existing applications. The Guardium for application encryption offers key management, signing, and encryption capabilities. This helps in the protection of files, database fields, and big data selections amongst others.
h. Guardium for Batch Data Transformation
This solution offers data masking services. It enables secure, fast, and efficient use of technological innovations in data warehouses, big data on-premises, and on the cloud, sharing databases with DevOps and outsourced data analysis.
Wrap Up
Data encryption solutions protect data from fraudsters who attempt to access sensitive information. Therefore, an appropriate data encryption and protection tool like the IBM Guardium can help you to effectively organize and manage data centrally and help you to enforce security best practices across your data repository in the medical facility.
Hopefully, the above-mentioned points elaborate on the need for a state-of-the-art encryption tool and also highlights how IBM Guardium is the best suitable one for the healthcare industry.


WRITE A COMMENT